In order to provide a patient with secure access to their medical records, it’s important to establish who they are (their identity) and what they are allowed to have access to. In technical terms, establishing identity is referred to as authentication and establishing what they are allowed to do is referred to as authorization.
When I log in to my online banking account, I have to input a username, password and a code from a reader (by inputting my debit card and entering my pin code). These are several authentication steps – technically known as two-factor authentication (2FA). As the combination of factors of authentication that I must provider include things that I know (password and pin) and also things that I have (debit card), this is a specialised type of 2FA called multi-factor authentication (MFA), which is more secure. Once my identity has been established, some part of the bank’s system figures out what I’m allowed to do. In my case, I’m authorised to have full access to a few accounts (current, savings and ISA’s) and also restricted access to a corporate account (which allows me to view transaction history only – i.e. I am not allowed to transfer, deposit money or request a change of the credit limit on this account). These rules are known as authorization.
When designing computer systems, it’s desirable to separate concerns. This is done by building modular systems, with each module being optimised to address a given concern (see SoC separation of concerns). In an identity context, there are several common concerns – authentication, authorization, storage of protected resources (e.g. stores of personal data) and also client applications which a person may wish to use to access their protected resources (e.g. a mobile banking app).
Separating identity concerns in this way allows for a single sign-on (SSO) scenario, in which a person is able to access many different protected resource with a single set of credentials. This is common with social identities for example, where you register for a new service or app and are offered the option to register with your Google or Facebook accounts. Obviously,
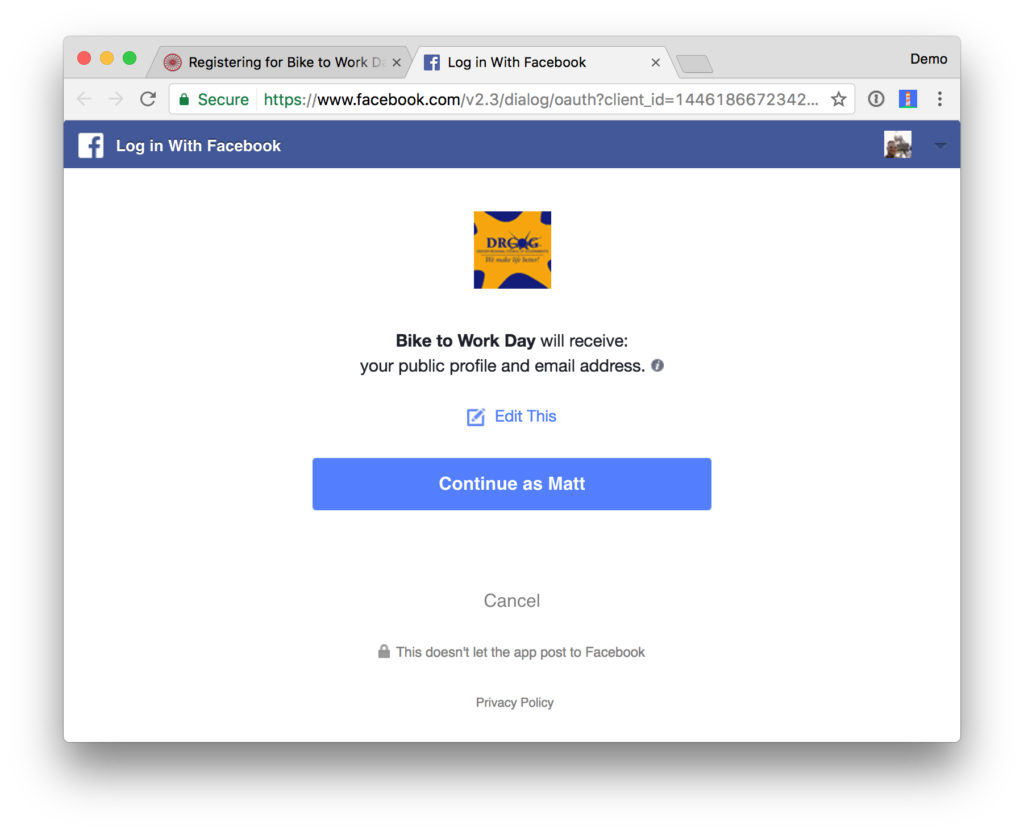
In the identity world, a number of common standards exist which define protocols for separating these concerns. The most popular, modern and widely used are OAuth 2.0. for authorization and Open ID Connect for authentication. These two standards work together hand-in-hand. These standards have led to the emergence of open source libraries, which greatly increase the speed to development (implementation), whilst simultaneously reducing the risk of implementation errors, introduced by developers who are not familiar with the standards.
NHS Digital (the UK’s national information and technology partner to the health and care system) has been working on a national, citizen identity system for several years. The system is called
Your NHS Account will be able to be used in the future, as a means to gain authorization to access national services. One such service is the National Events Management System (NEMS), which is currently under development by NHS Digital. This system offers the potential of access to your medical records, which will flow nationally between
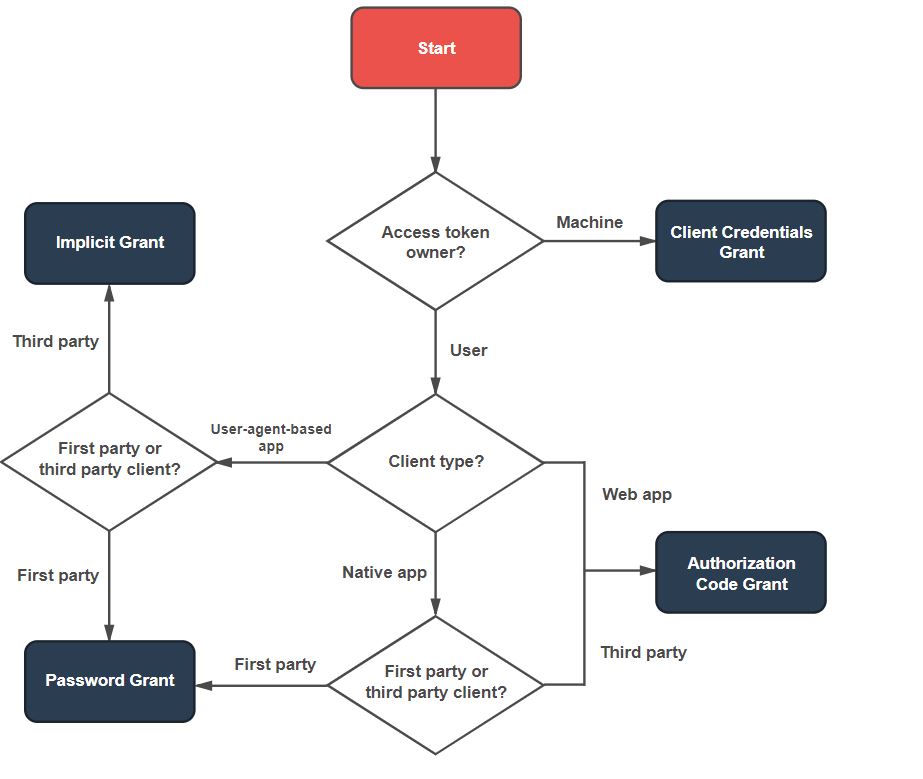
The NHS Login service will support OAuth 2.0. and Open ID Connect, which is a welcome move. Underneath these protocols are a number of alternative grant flows. It will be important for clients to have access to and to select the right grant flows. This will depend on factors such as the client type (e.g. whether the client is public or private).
The NHS Login service will be one of the first national services to provide secure but public access over the Internet. Again, this is a welcome move, as it greatly reduces the burden and downstream cost on integrating parties, and ultimately, to system commissioners (as opposed to the old and expensive private wide area network infrastructure – N3 / HSCN). This is also in line with the UK Government’s (public) cloud first policy.
Initially, NHS Login will not allow a patient to delegate access (for example, an elderly mother with early onset of dementia, delegating access to her daughter, in order to help manage her care). Neither will it allow proxy access (for example where a parent may be given access to their child’s medical records). However, these are two concepts which NHS Digital are considering for future releases.
Be First to Comment